An established set of guidelines that govern how data is transferred between various devices connected to the same network is known as a network protocol.
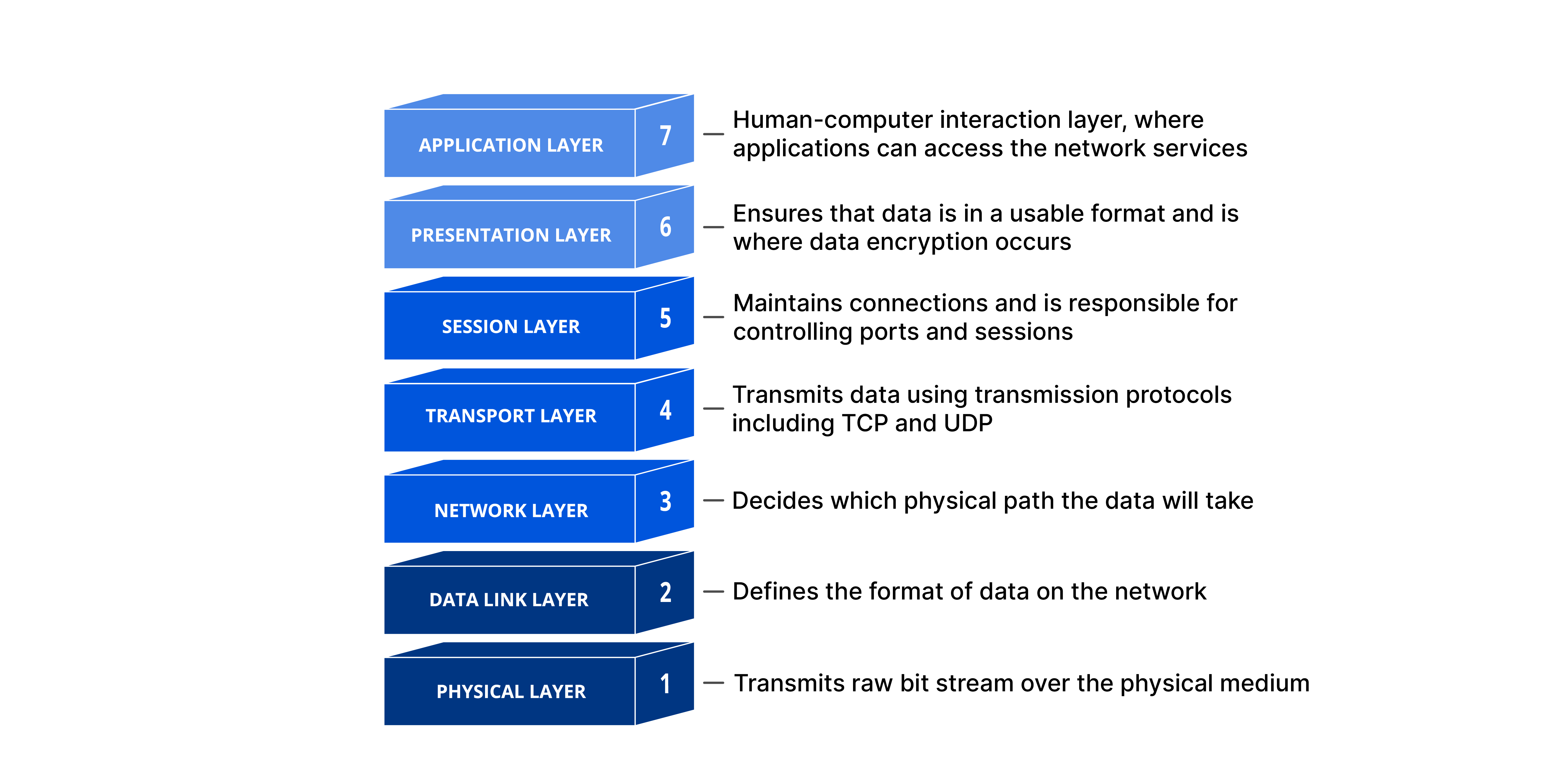
At the top of the OSI model is the application layer. Users interact with each other through this layer. The user receives services from it. Any kind of application or communication process requires the performance of a variety of functions by the application layer.
Application Layer Protocol
1. HTTP
- HTTPS, which stands for Hypertext Transfer Protocol Secure, is the more secure form of HTTP, which is what HTTP stands for.
- Data from the World Wide Web is accessed via this protocol.
- Pages in a text document are linked together using the well-organized documentation system known as hypertext.
- The client-server concept is the foundation for HTTP.
- It establishes connections using TCP.
- Due to the statelessness of the HTTP protocol, the server does not keep track of the client's prior requests.
- For connection establishment, HTTP uses port 80.
2. FTP
- File Transfer Protocol is referred to as FTP.
- The protocol is what allows us to transfer files.
- Any two machines using it can facilitate this. FTP, however, is both a program and a protocol.
- FTP encourages file sharing between distant computers through dependable and effective data transfer. For FTP, the data port is 20 and the control port is 21.
3. DNS
- Domain Name System is what it stands for.
- Therefore, a DNS server must convert each time a domain name is used into the corresponding IP address.
- The translation of www.abc.com, for instance, could be 198.105.232.4.
- 53 is the port number for DNS.
4. SMTP
- It stands for Simple Mail Transfer Protocol.
- A component of the TCP/IP protocol, it.
- SMTP transfers your email on and across networks by use of a procedure known as "store and forward."
- To get your communication to the appropriate computer and email inbox, it closely collaborates with a component known as the Mail Transfer Agent (MTA). The SMTP port number is 25, and it.
5. POP
- POP stands for Post Office Protocol, and POP3 (Post Office Protocol version 3) is the most recent version.
- User agents utilize this straightforward protocol to retrieve messages from mail servers.
- POP protocol operates on port 110.
- It establishes connections using TCP.
- POP operates in two modes: Keep Mode and Delete Mode.
- Once the messages have been downloaded to the local system, the Delete mode deletes them from the mail server.
- Keep mode allows users to read their emails from the mail server at a later time while without deleting the message from the mail server.
6. Telnet
- Telnet stands for the TELetype NETwork.
- In terminal emulation, it is helpful.
- It enables Telnet clients to access the Telnet server's resources.
- On the internet, it is utilized for file management. Devices like switches are first set up using it.
- The telnet command is a command that connects to a remote system or device using the Telnet protocol. Telnet uses port number 23.
Transport Layer
- In the TCP/IP model, the transport layer is the second layer; in the OSI model, it is the fourth layer.
- In order to deliver messages to a host, it is an end-to-end layer. It is referred to as an end-to-end layer since it offers a point-to-point connection between the source host and destination host rather than a hop-to-hop connection to deliver the services effectively. In the Transport Layer, a segment is the basic unit of data encapsulation.
- From the perspective of the sender, the transport layer receives data (messages) from the application layer, splits the data, adds the source and destination ports to the header of each segment, and sends the message to the network layer.
- The transport layer receives data from the network layer, segments it, reads its header, determines the port number, and then passes the message to the correct port in the application layer.
1.UDP
- A Transport Layer protocol is called User Datagram Protocol (UDP).
- The Internet Protocol family, also known as the UDP/IP suite, includes UDP. It is an unreliable, connectionless protocol, unlike TCP. Therefore, there is no requirement for a link to be established before data transfer. Low-latency and loss-tolerant connections can be established over the network with the aid of UDP. Process to process communication is made possible through UDP.
- Process to process communication is made possible through UDP.
Network Layer Protocol
ARP
- The media access control (MAC) address of a device is one example of a physical address to which an IP address can be mapped using this protocol.
- This enables networked devices to communicate with one another.
RARP
- A physical computer in a local area network (LAN) can utilize the Reverse Address Resolution Protocol (RARP) to ask for its IP address.
- This is accomplished by transmitting the device's physical address to a dedicated RARP server on the same local area network (LAN) that is watching for RARP requests.
ICMP
- Between devices on a network, this protocol is used to send error messages and other types of information.
- It is frequently used to provide diagnostic data or troubleshoot network problems.
IGMP
- It stands for Internet Group Message Protocol
- Two types of communication:
- Unicasting - One-to-one communication
- Multicasting- One-to-many communication
- It is used by the hosts and router to support multicasting and moreover to identify the hosts in a LAN.
IP
- It is a set of rules for routing and addressing packets of data
- The information in IP is attached to each packet which helps router to send packets to the right place.
- Once the packets arrive at their destination, they are handles differently depending on which transport protocols is used in combination with IP.
- Types of IP Address:
- Static IP address is the one which is manually created as opposed to having been assigned and cannot be change.
- Dynamic IP address is the one which is assigned by Dynamic Host Configuration Protocol (DHCP) server and it can be changed.
- Classes of IP address: IP address defines five classes ; A, B, C, D and E each having range of valid IP addresses. The first three IP address can be used as host address and the last two are used for multicast (D) and for experimental purpose (E).
Class A IP address has the first octet starting from 0.
Class B starts from 0+128 = 128.
Class C starts from 0+128+64=192.
Class D starts from 0+128+64+32=224.
Class E starts from 0+128+64+32+16=240.
Class A ends at 127, which can be inferred from the starting end of Class B.
Similarly Class B ends at 191.
Class C ends at 223.
Class D at 239.
Class E at 255.
Network Access Layer
- The TCP/IP protocol hierarchy's Network Access tier is the bottom tier.
- The protocols in this layer give the system the tools to send data to the other gadgets on a network to which it is directly connected. It specifies how to send an IP datagram over the network.
- In contrast to higher-level protocols, Network Access Layer protocols need to be aware of the specifics of the underlying network (its addressing, packet structure, etc.) to format the data being transferred in a way that complies with network requirements.
- All of the operations performed by the Data Link and Physical layers at the bottom of the OSI reference model can be included in the TCP/IP Network Access Layer.
Ethernet
- The standard method for establishing connections between devices in a wired LAN or WAN is Ethernet.
- It allows for the use of a protocol, which is a set of guidelines or common network language, to allow devices to communicate with one another.
Ethernet Types
1. Fast Ethernet: Supported by twisted pair which is quite a high-speed internet and can transmit or receive data about 100Mbs.
2. Gigabit Ethernet: Data is transferred over this type of network at a rate of roughly 1000 Mbps or 1Gbps. Fast Ethernet is being replaced with Gigabit speed, which is an improvement. The data transfer speed in this kind of network is influenced by each of the four pairs in the twisted pair cable.
3. 10-Gigabit Ethernet: With a data transfer rate of 10 Gigabit/second, this form of high-speed network is even more modern and efficient. This network area can be expanded up to about 10,000 meters by employing a fiber optic cable.
4. Switch Ethernet: This network type needs a switch or hub. Additionally, a standard network cable is used in this instance rather than a twisted pair wire.
Subnetting
- Subnetting is a method of dividing a single physical network into logical sub-networks (subnets).
- Local devices are connected to other networks through the equipment known as a gateway or default gateway. This means that a local device must submit its packets to the gateway before they may be forwarded to their intended recipient outside of the local network when it wishes to communicate information to a device with an IP address on another network.
Subnet Mask
- By setting the host bits to all 0s and the network bits to all 1, a 32-bit integer known as a subnet mask is produced. The subnet mask divides the IP address into the network address and host address in this manner.
- A broadcast address is always associated with the "255" address, while a network address is always associated with the "0" address. Both are set aside for these specific uses, hence neither can be allocated to hosts.
- Most networks employ the Internet Protocol as the underlying structure to enable device communication, which is made up of the IP address, subnet mask, and gateway or router.
Classful Routing
- Subnet masks are not imported by Classful Routing. Subnet mask is also provided in this case following the route modification.
- A method of allocating IP addresses called classful addressing divides addresses into five main categories.
- The above image demonstrates how the subnet mask in classful routing is constant across all devices and does not change.
Classless Routing
- In order to slow down the rapid expiration of IP addresses, classless addressing will eventually take the place of classful addressing.
- Subnet mask is imported by classless routing, which makes use of triggered updates. VLSM (Variable Length Subnet Mask) and CIDR (Classless Inter-Domain Routing) are supported in classless routing.
- Hello messages are used for status checking in classless routing. In classless routing, subnet masks may not always be the same for all devices; we can see this in the example image.
Variable Length Subnet Mask (VLSM)
- In VLSM, the subnet design employs several masks within a single network, i.e., multiple masks are utilized for various subnets within a single class A, class B, or network.
- Due of the varying size of subnets, it is utilized to make them more usable. Additionally, it is described as the procedure of subnetting a subnet